Despite the rise of the information security market, traditional cybersecurity has long been based on perimeter defenses. The assumption was simple: once you’re inside the network (whether through a VPN or physical access), you’re trusted.
Firewalls, intrusion preventers, and virtual private networks were all aimed at this idea of a secure inner world separated from an untrusted outer world.
But with companies shifting to cloud-first, hybrid work, and multiplexed partner ecosystems, these traditional security perimeters began to break down. An end user could be sitting in a home office, a coffee shop, or halfway around the world and still need access to enterprise systems in a secure way.
At the same time, cyber crimes became more sophisticated, exploiting any vulnerability from within after perimeter security has been compromised.
What Is Zero Trust Architecture?
Zero Trust is a security framework established on one easy principle: never trust, always verify.
Unlike the previous models that by default trust users and devices once inside the network, Zero Trust tracks each request for access, where it’s coming from, what device is used, and who the user is.
It relies on the presumption that nothing in the system is entirely secure by design and continually authenticates access through multiple dynamic factors.
| Traditional Security | Zero Trust Architecture |
| Trusts internal users and devices | Trusts no one by default |
| Focuses on perimeter protection | Focuses on identity and access control |
| Flat internal network | Segmented network with least privilege access |
| Occasional security checks | Continuous verification and monitoring |
How ZTA Differs from Traditional Security
Core Principles of Zero Trust Architecture
A Zero Trust network always relies on a well-defined, real-world set of principles that maintain the system’s security posture regardless of where users or devices come from.
1. Identity Verification
Before anyone can access anything, their identity must be verified. It’s no longer just a password; it might include multi-factor authentication (MFA), device authentication, or even biometric authentication.
The purpose is to ensure that the person (or device) that’s trying to connect is indeed who they say they are.
2. Least Privilege Access
Once an individual has been authenticated, they’re only provided with access to the exact data or system they need to have — nothing more. This limits possible harm if an account is ever compromised.
This way, users will only possess sufficient privileges to get their work done, and no more permissions.
3. Steady Monitoring
A Zero Trust security model doesn’t stop checking after the first login. It keeps watching in real time users’ behavior, the state of devices, location, and so on. If something seems suspicious, the system can shut down access or trigger a new check.
4. Microsegmentation
Instead of having one massive network with everything connected, Zero Trust separates things into small segments. Each segment has its own set of controls and rules. So even if the intruder gets into one segment, it can’t easily move to another one.
How Zero Trust Security Architecture Works in Practice
Zero Trust is not only a security principle; it’s a practical way of protecting systems. Let’s see how it works in the real world with an example.
Example: A Remote Employee Accessing a Company System
Let’s take the case of a remote worker who needs to log in to the organization’s internal financial application.
The employee tries to log in with their username and password.
- User and Device Are Verified
Before letting them in, the system checks:
- Is this really the right person? (using, for instance, multi-factor authentication)
- Is the device safe and approved? (e.g., up-to-date software, no signs of tampering)
- Is the request coming from a secure area?
These checks are regulated by identity and access management and software-defined perimeter tools.
- Access Is Granted But Only What’s Needed
If everything looks good, access is allowed, but only to what the employee needs. A financial analyst, for example, can view reports but not modify system settings. This is the least privilege principle.
As the user operates, their behavior is followed in real time by a security information and event management (SIEM) system. If something fishy happens (like trying to download large files or access restricted zones), access can be denied or audited.
Even if someone breaks in, they won’t get far. Microsegmentation puts each part of the system in an isolated environment, so attackers cannot simply walk from one piece to another.
Tools That Make It Work
As seen above, Zero Trust access is built on a set of integrated tools that talk to one another and verify users, guarantee network security, prevent security breaches, and monitor activity in real time:
- IAM (Identity and Access Management): Manages user logins and permissions.
- SDP (Software-Defined Perimeter): Gives or blocks app access depending on who users are and where they’re from.
- MFA (Multi-Factor Authentication): Incorporates extra verifications like a text code or app approval.
- SIEM (Security Information and Event Management): Monitors for suspicious behavior in real time.
Benefits of Zero Trust for Enterprise Systems
Two years ago, enforcing a Zero Trust architecture was a priority for a majority of companies.
By 2032, by the way, the entire Zero Trust market is believed to be estimated at around $133 billion, up from around $32 billion in 2023. But what are the real, tangible benefits for modern enterprise networks?

One of the greatest benefits is that Zero Trust network access shrinks the attack area. Because no user and no device are trusted by default, each request for access must be authenticated.
That means it is much harder for attackers to make their way through the system, even if they do manage to get in.
Also, ZTA gives companies more control over users’ access. Instead of mere static user roles, Zero Trust takes into account the entire context (i.e., the person’s identity, device, location, and behavior) to decide what they should be able to see or do.
Third, Zero Trust is visibly effective for remote and hybrid work. Employees are able to access business systems from any location, without the use of a VPN or presence in the office.
Finally, Zero Trust provides better visibility across the system. Since it is always focusing on the user and the device, security teams can identify potentially malicious activity early and react quickly.
Examples of Zero Trust Security Solutions in Action
There are various prominent businesses and sectors employing Zero Trust Architecture to improve protection while allowing remote access. These examples illustrate how the practice is executed in real life.
Google’s BeyondCorp is quite possibly the most famous example. In response to a major cyberattack in 2009, Google moved away from relying on VPNs and started working on an architecture in which access is based on user context and identity, not on a network location.
That enabled employees to be able to work securely anywhere without necessarily having to be on a trusted internal network. BeyondCorp was one of the initial real-world Zero Trust architectures.
Microsoft
Microsoft also uses Zero Trust across its Microsoft 365 and Azure solutions. It relies on strong identity checks, persistent monitoring, and Conditional Access and Defender for Identity tools to manage access and stop threats in real time. Users only get access to what they need, and the system watches for unusual activity around the clock.

Other Organizations
Many less prominent financial, healthcare, and government organizations are also adopting Zero Trust. For example, healthcare facilities control access to patient data by role and device security.
Banks divide their networks in such a manner that if one is attacked, it is not easily going to spread to the others. It protects the sensitive data without interrupting smooth processes.
Challenges and Considerations of Zero Trust Systems
In 2024, when asked about their intentions to adopt Zero Trust, 30% of respondents (who were cybersecurity professionals) admitted that they were working with several security vendors to develop a plan to incorporate Zero Trust and reduce security risks.
23% of answerers, in turn, stated they had already started implementing Zero Trust. By contrast, 47% of respondents claimed not to be ready yet to adopt Zero Trust. But why?
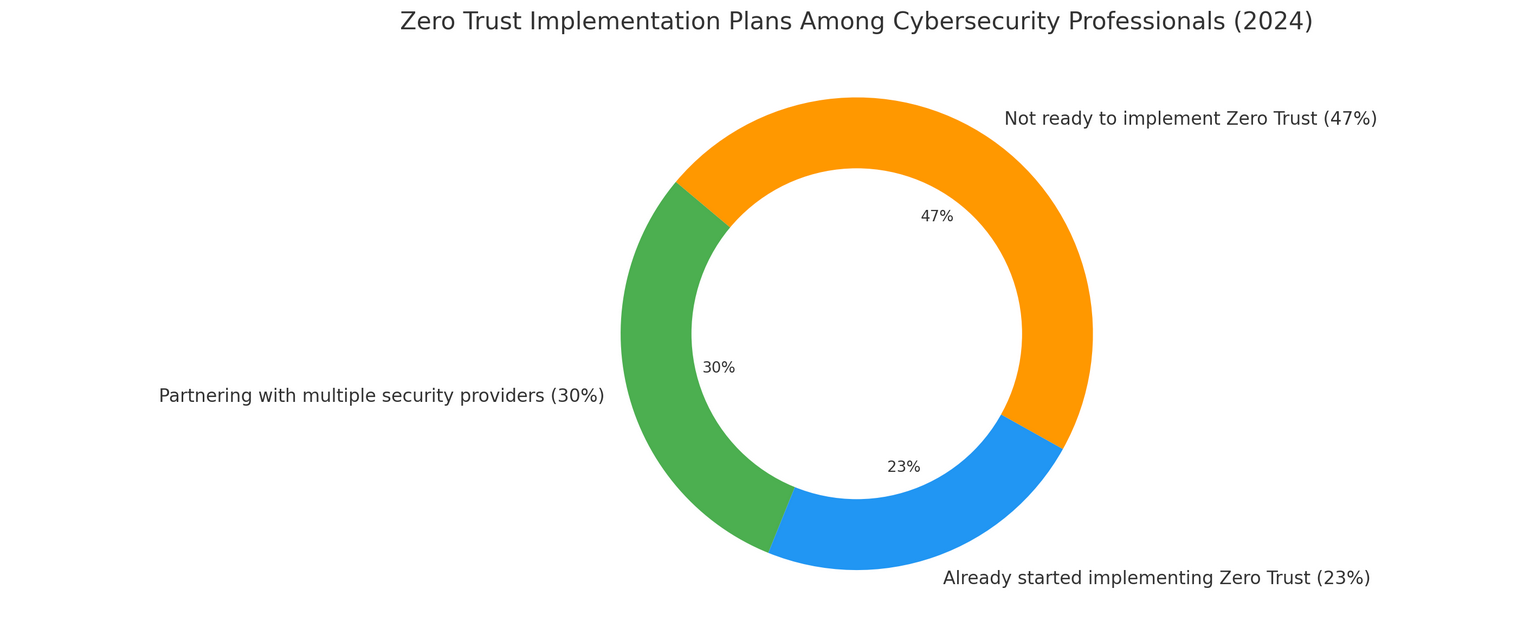
Zero Trust Implementation Among Cybersecurity Professionals in 2024
First, Zero Trust often means rethinking how your systems are built. Traditional security models were based on trusting everything inside the network.
With Zero Trust, that model changes completely. You’ll need to redesign how users, devices, and applications connect, which may include reorganizing access rules, segmenting the network, and updating older systems.
Second, you’ll likely need to invest in new tools and processes. Zero Trust usually involves adding identity and access management, multi-factor authentication, endpoint protection, monitoring tools, and software-defined perimeter solutions. These tools have to work together, which can take some time and planning.
Another thing is that the Zero Trust environment is not an install-and-forget configuration. It requires systematic updates: access policies and security measures must be changed when teams grow, roles shift, or new tools are added.
It also requires good communication across business units, security teams, and IT to guarantee the system works well for all parties.
Sometimes, companies also face resistance to change. Users have probably got used to free access or simplified login processes, and more stringent controls will therefore initially seem like a nuisance.
That is why it pays to roll out Zero Trust policies in phases, exactly state the reasons for doing so, and provide training to your personnel.
How to Implement Zero Trust Architecture
It is fair to state that Zero Trust isn’t an immediate remedy; it’s a continuing process. In 2024, most companies had already started adopting a Zero Trust strategy or cooperating with security vendors to create a roadmap. But how do you begin the process in a way that actually works?

The main thing to remember before Zero Trust implementation is that putting it into action doesn’t happen all at once; it’s a gradual process that takes careful planning and the right tools.
The first step is to audit your current environment. That means specifying all users, endpoints, applications, and data in your organization.
From there, you can begin to put more rigid identity and access controls in place using solutions, such as identity and access management solutions and multi-factor authentication.
Next, implement the least privilege principle: users should only have the access they actually need. No more. At the same time, deploy microsegmentation to compartmentalize the most critical elements of your system, so even if something goes wrong, it is easier to contain the issue.
As you move forward, it’s important to monitor activity in real time. Security information and event management systems can help you:
- Spot unusual user behavior before it becomes a problem.
- Catch threats early and respond quickly.
- Update access controls automatically based on changing risk levels.
We recognize that making a comprehensive Zero Trust solution may seem overwhelming, especially if your company lacks the in-house resources or available time to do it on your own.
That’s where SCAND comes in. We help organizations develop and implement Zero Trust software adapted to their exact needs, whether you’re greenfielding or upgrading an existing implementation.
In projects involving remote access, sensitive data, or hybrid environments, we:
- Use IAM frameworks to enforce least privilege access.
- Integrate MFA and SDP tools for identity- and context-aware authentication.
- Design infrastructure with microsegmentation, container isolation, and secure APIs.
- Continuously monitor and enhance security policies using SIEM and behavior analytics tools.
- Apply secure DevOps practices that go in line with the Zero Trust approach, from development to deployment.
- Embed generative AI in cybersecurity to further improve protection.
If you reconsider your enterprise architecture or change to the cloud, now is the perfect moment to learn about Zero Trust principles. Let us hear from you at SCAND and discover how we can help you design robust security systems that can prevent any attacks.
Frequently Asked Questions (FAQs)
Is Zero Trust only for large enterprises?
No. Any organization can adopt and benefit from Zero Trust, especially if they need cloud security to support remote work.
Do I need to get rid of my VPN and other security tools before implementing a Zero Trust system?
Not necessarily, but VPNs often represent a single point of trust. Zero Trust works as a more dynamic and secure alternative.
How long does it take to implement ZTA?
It depends on your security infrastructure, but most organizations adopt it gradually, starting with identity and access security controls.
Can SCAND help implement Zero Trust security systems?
Absolutely. Whether you want to start from scratch, modernize traditional perimeter-based security, or even extend Zero Trust (if you already have it), we can offer the right approach for your business.
